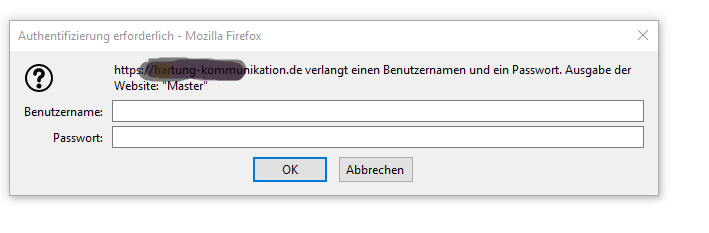
As you are already using Apache as your 'frontend' (reverse) proxy, just change the listening port of your nginx and tell apache to fetch content there. This is done by changing the listen parameter in your nginx config, for example to 8443. Bitwarden + apache reverse proxy: selfhosted.
Latest versionReleased:
Keyring backend reading password data from Bitwarden
Project description
Implementation of the Keyring backend code reading secrets from Bitwarden using Bitwarden-cli
Overview
The Keyring python package provides a handy single point of entry for any secret holding system, allowing for seemless integration of those systems into applications needing secrets, like twine.
This projects implement Keyring to be able to read secrets from Bitwarden, an open source multiplatform cloud/self-hostable password manager.
This backend assumes that it will be used in the context of a CLI application, and that it can communicate with the user using sdtin, stdout and stderr. We could implement an additional backend for use in a library assuming that everything is already unlocked, or another one using pinentry to ask the user.
Requirements
This project uses the official bitwarden CLI under the hood, because there's no simple official Python bitwarden lib. Here are the installation instructions as of October 2018 and the link to the up to date instructions
You can install the Bitwarden CLI multiple different ways:
NPM
If you already have the Node.js runtime installed on your system, you can install the CLI using NPM. NPM makes it easy to keep your installation updated and should be the preferred installation method if you are already using Node.js.
Native Executable
Natively packaged versions of the CLI are provided for each platform which have no requirements on installing the Node.js runtime. You can obtain these from the downloads section in the Bitwarden documentation.
Other Package Managers
Installation and configuration
The Python packaging ecosystem can be quite a mess.
Because of this, it's likely that your setup and my setup are nothing alike. Keyring supports a configuration file with an option allowing to explicitely define the path to a backend. You may need that for your installation, or maybe not.
Usage
Use as a normal keyring backend. It is installed with priority 10 so it's likely going to be selectedfirst.
If you want to use it with twine, good news, you're already set. Just make sure that this package is installed in the same location as twine.
bitwarden-keyring will automatically ask for credentials when needed. If you don't want to unlock your vault every time, export the vault session to your environment (use bw unlock and follow the instructions, or launch export BW_SESSION=$(bw unlock --raw)).
Caveats
bitwarden-keyring was only tested with:
- macOS, using the
bitwarden-clifrombrew - ubuntu, using the
bwfromsnap
As mentionned, bitwarden-keyring only works in the context of a CLI application with access to standard inputs and output. If you need something that either reads silently or using another method of communication, the best is probably to make another backend and most of the functions can be reused.
Licensing
bitwarden-keyring is published under the terms of the MIT License.The name Bitwarden is most probably the property of 8bit Solutions LLC.
Contributions and Code of Conduct
Contributions are welcome, please refer to the Contributing guide.Please keep in mind that all interactions with the project are required to follow theCode of Conduct.

Release historyRelease notifications | RSS feed
0.3.0
0.2.1
0.1.2
0.1.1
0.1.0
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
| Filename, size | File type | Python version | Upload date | Hashes |
|---|---|---|---|---|
| Filename, size bitwarden_keyring-0.3.0-py2.py3-none-any.whl (6.7 kB) | File type Wheel | Python version py2.py3 | Upload date | Hashes |
| Filename, size bitwarden-keyring-0.3.0.tar.gz (5.4 kB) | File type Source | Python version None | Upload date | Hashes |
Hashes for bitwarden_keyring-0.3.0-py2.py3-none-any.whl
| Algorithm | Hash digest |
|---|---|
| SHA256 | 5825f09eccd2df50213c3f0db0bd2c4d2c411ba4faf4c8d4d98329ba23cce32d |
| MD5 | 34d3c4740d2b131bb3e0e6e2d5fa9be6 |
| BLAKE2-256 | c58c0c5eedfd0c19c9b5ca081f808f13a2a456f21e839061840d4e274cf3ae70 |
Hashes for bitwarden-keyring-0.3.0.tar.gz
| Algorithm | Hash digest |
|---|---|
| SHA256 | 1beb1bb103074fbed1ca5a3a7863b8f8f000c2a2e96a28a6dbe276b909674351 |
| MD5 | c9b97e5fb9979f578593d0786b638154 |
| BLAKE2-256 | 3017b9d1e0ffade8c178cbf0d3ea469ef209f6f9967787a5018e7581fa102ea5 |
Password managers are very useful utilities that store (and generate) unique and lengthy passwords. Many utilities exist to store passwords locally (pass, EncryptionWizard, etc), but I need my passwords synced across several devices. Dozens of password managers exist that perform multi-device sync. But, many services require storing passwords on their servers. Some allow storing encrypted stores on your cloud (Dropbox, OneDrive, etc). However, I want my password stores to exist 100% under my local control. ARM development boards, like the Beagle Bone Black Wireless, provide a nice low-cost, low-power platform to run a password manager store. Additionally, the device can be easily powered down to take the password store offline. A Raspberry Pi should also work, but I was lacking one on hand.
Bitwarden is the only open source password manager I've discovered that allows self-hosting the server and also provides open source iOS, Android, Linux, OS X, and Windows clients. Unfortunately, the official Bitwarden server does not support ARM because of a mssql dependency. Joshua Stein wrote a nice Ruby server supporting the Bitwarden API that can be self-hosted on ARM devices. (Servers written in golang and Rust also exist.)
Running rubywarden on the Beagle Bone Black Wireless only allows syncing passwords between devices when they are on the same network as the BBBW. Trading the 'inconvenience' of local-only sync for 100% control of my password store is well worth it, in my opinion.
Note: 8bit Solutions LLC has graciously open sourced Bitwarden. Show your support for open source companies by purchasing a premium membership even if you self-host. High quality software does not write itself.
Initial Setup
- Install dependencies
# apt-get install bundler libsqlite3-dev
# gem install bundler
- To slightly improve security, a utility account named
rubywardenwill be used to run the server.
Bitwarden_rs Apache

# adduser --disabled-password --disabled-login rubywarden
Clone the
rubywardenrepository into/opt$ cd /opt
# git clone https://github.com/jcs/rubywarden
# chown -R rubywarden /opt/rubywarden
# sudo su rubywarden
Create the necessary directory structure for
rubywarden$ cd rubywarden
$ mkdir -p db/production
Install the necessary ruby dependencies
$ bundle install
Before the first run, the
rubywardendatabase must be initialized$ env RACK_ENV=production bundle exec rake db:migrate
rubywardendoes not allow new user sign-up unless the environmental variableALLOW_SIGNUPSis true. To launch the server and allow sign-ups run the following command. Subsequent launches do not require the environmental variable.$ env RACK_ENV=production ALLOW_SIGNUPS=1 bundle exec rackup -p 4567 config.ru
Bitwarden provides a variety of client installs. Choose the appropriate one and click the gear icon on the splash screen to add the self-hosted server.
- Create an account and start managing passwords! Note: If testing with the iOS client, please read the dedicated iOS section below.
systemd
It's really useful to have rubywarden run when the BeagleBone is powered up. Writing a systemd unit file to provide startup functionality is fairly straightforward.
Bitwarden Apache
Create /etc/systemd/system/rubywarden.service and add the following:
Enable and start the service. Use journalctl -u rubywarden to debug any issues.
Compatility with iOS app
The Bitwarden AppImage seems to function just fine without rubywarden using HTTPS. By default, it is only using HTTP. However, the iOS client requires HTTPS.
In order to support HTTPS, the Apache webserver (already running on the BBBW) will be configured to serve HTTPS and function as a proxy to the rubywarden server. Since rubywarden is not internet accessible, Let's Encrypt certificates don't make sense; instead a self-signed certificate will be used for HTTPS. In order for the self-signed certificate to be usable on iOS, a Certificate Authority certificate will need created and installed on the iOS device.
Note: Apple changed trusted certificate requirements in iOS 13 requiring an extendedKeyUsage flag to be set in the certificate.
Bitwarden Docker Apache
Create the CA certificate
$ openssl genrsa -out rubywardenCA.key 2048
$ openssl req -x509 -sha256 -new -key rubywardenCA.key -out rubywardenCA.crt -subj /CN='rubywarden CA'
Send the
rubywardenCA.crtcertificate to the iOS device via e-mail and follow the prompts to install. After installation, use the Settings app to navigate toGeneral->About->Certificate Trust Settingsand togglerubywarden CAon. This means that iOS will treat any certificate signed by the CA as a valid HTTPS connection.Generate a certificate for Apache to use
$ openssl genrsa -out rubywarden.key 2048
$ openssl req -new -out rubywarden.req -key rubywarden.key -subj /CN=beaglebone.local
$ openssl x509 -req -sha256 -in rubywarden.req -out rubywarden.crt -CAkey myCA.key -CA myCA.cer -days 365 -CAcreateserial -CAserial serial -extfile <(printf 'extendedKeyUsage = serverAuthnsubjectAltName=DNS:beaglebone.local')
The keys created above can be used to perform mitm attacks if they are compromised. To improve security (slightly, the SD card can just be removed from the BBBW) move them to
/root/certs/beaglebone.local/and make the keys read-only.# mkdir -p /root/certs/beaglebone.local/
# mv rubywarden.* /root/certs/beaglebone.local
# chmod 400 /root/certs/beaglebone.local/*.key
Finally, set up Apache to serve as an HTTPS proxy. Append the following VirtualHost entry to
/etc/apache2/sites-enabled/000-default.confRelaunch Apache with# systemctl restart apache2.serviceafter making the edits.
Bitwarden Apache2
Did your security posture improve because of this post? Consider saying thanks by using my Amazon Affilliate URL and help to keep this site ad & analytics free.
